We offer a variety of protocols: OpenVPN, WireGuard, Shadowsocks, VLESS, VMess, Trojan. Each of them has its own advantages, which you can use to suit your needs.

Choose downloaded configuration file or copy file content and connect
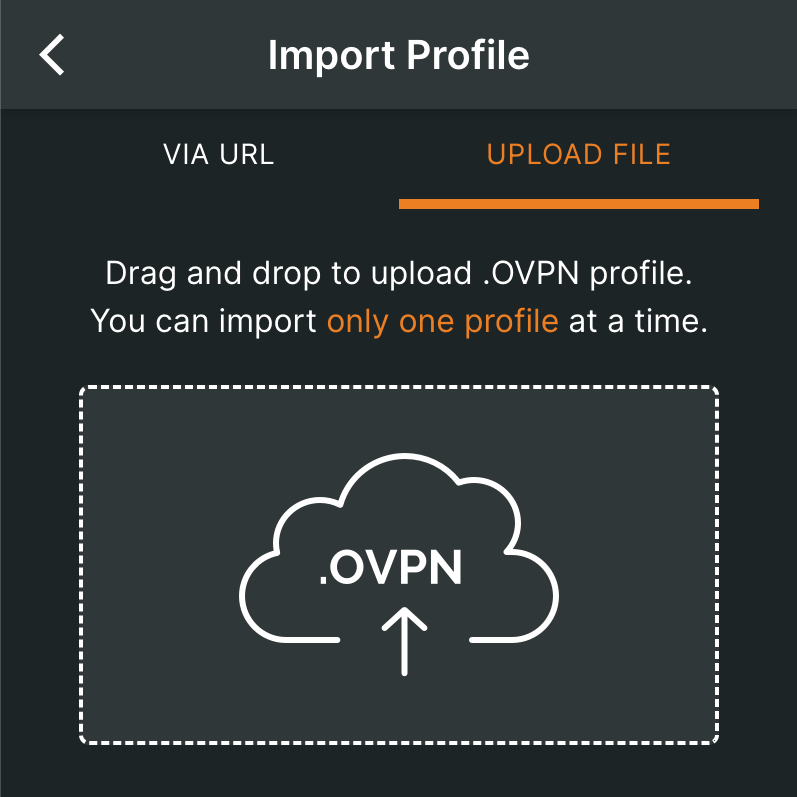

Choose downloaded configuration file or copy file content and connect
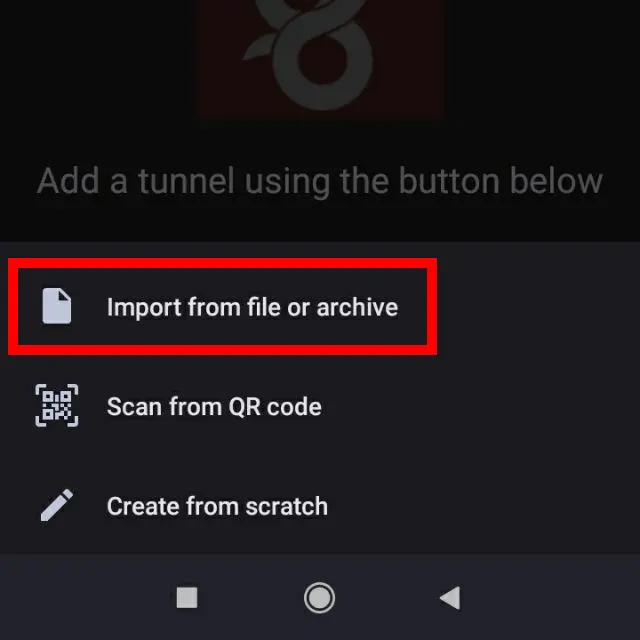

Choose downloaded configuration file or copy file content and connect
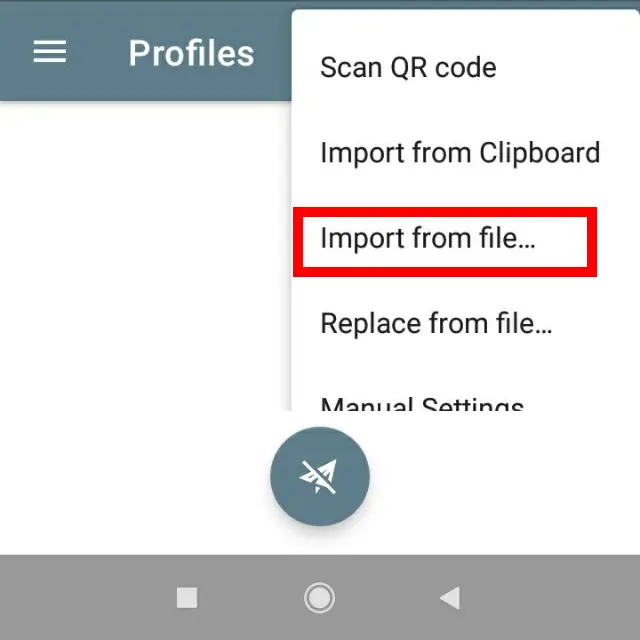

Choose downloaded configuration file or copy file content and connect
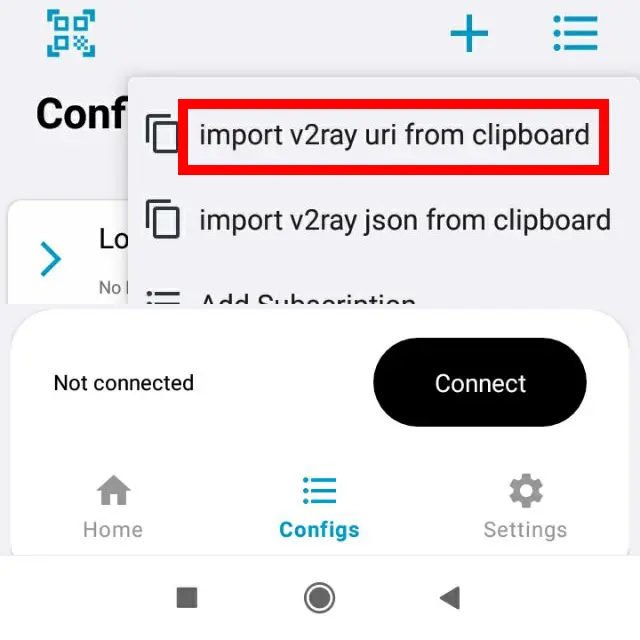

Choose downloaded configuration file or copy file content and connect


Choose downloaded configuration file or copy file content and connect

You can top up your balance using your personal XMR address. The amount will be credited to your account balance in USD at the current exchange rate.The funds are credited within 5 minutes. We recommend saving the transaction hash in case of possible problems.
Minimum commission upon payment. Monero (XMR) is a privacy-focused cryptocurrency that aims to provide users with enhanced anonymity and security in their financial transactions. It was launched in April 2014 as a fork of the Bytecoin cryptocurrency. Monero is built on the principles of privacy, decentralization, and fungibility.
You can top up your balance using cryptocurrency via Cryptocloud. If you do not have a cryptocurrency, you can exchange it there or anywhere else. The amount will be credited to your account balance in US dollars at the current exchange rate.Funds are credited within 5 minutes. It is recommended to save your payment information in case of trouble with payment.
We will add your balance in USD as soon as we receive confirmation from CryptoCloud. We recommend that you save the payment link in case of possible problems. CryptoCloud supports a wide range of currencies, giving you the freedom to transact globally without the hassle of currency conversions. Whether you're a seasoned crypto enthusiast or a newcomer, that platform makes it easy for you to make payments with confidence.
Money-Back Policy
We strive to provide quality services and ensure your satisfaction. This Money-Back Policy outlines the terms and conditions under which we offer refunds. To be eligible for a refund, you must meet the criteria specified in the respective product or service's terms and conditions:
Timeframe: Refund requests must be submitted within 3 days from the date of purchase or service initiation.
Operability: The purchased service must be in an inoperable state (i.e. without the ability to establish a VPN connection)
Refunds are subject to approval by our team. We reserve the right to deny a refund request if it does not meet the specified eligibility criteria.
We are not responsible for every protocol working in you location. If certain protocols are blocked in your location, we recommend to choose the appropriate protocol.
Refunds are made only through Monero XMR.
To request a refund, please contact our customer support team at [email protected] with the detailed reason explanation of the refund request.
The use of the service is regulated by the corresponding Terms of Use and Privacy Policy.
By using the Service, you acknowledge that you have read, understood, and agree to be bound by these Terms and Conditions.
In case of repeated, systematic violation of these Rules, we reserve the right to completely suspend the provision of services.
Last updated: January 1, 2024
This privacy policy for PonVPN describes how and why we might collect, store and process your information when you use our services, such as when you:
If you do not agree with our policies and practices, do not use our services. If you still have any questions or concerns, contact us at [email protected]
The following definitions shall have the same meaning regardless of whether they appear in singular or in plural.
For the purposes of this Privacy Policy:
Account means a unique account created for You to access our Service or parts of our Service.
Company (referred to as either "the Company", "We", "Us" or "Our" in this Agreement) refers to PonVPN
Cookies are small files that are placed on Your computer, mobile device or any other device by a website, containing the details of Your browsing history on that website among its many uses.
Device means any device that can access the Service such as a computer, a cellphone or a digital tablet.
Personal Data is any information that relates to an identified or identifiable individual.
Service refers to the Website or Telegram Bot.
Usage Data refers to data collected automatically, either generated by the use of the Service or from the Service infrastructure itself (for example: logs about purchasing and balance popup. it is neccessary in case of software errros).
Website refers to ponvpn.com
You means the individual accessing or using the Service, or the company, or other legal entity on behalf of which such individual is accessing or using the Service, as applicable.
While using Our Service, We may ask You to provide Us with certain personally identifiable information that can be used to contact or identify You. Personally identifiable information is limited to:
Email address (if provided)
Telegram ID (if you are using our Telegram Bot)
Usage Data
Usage Data is collected automatically when using the Service.
Usage Data is information such as:
Which services have you bought via our Service and when did you do that (it is neccessary for billing purposes)
We dont collect the type of device You use, Your device unique ID, Your operating system, the type of Internet browser You use, unique device identifiers and other diagnostic data.
We use Cookies to store certain information. This information is limited to:
The PonVPN may use Personal Data for the following purposes only:
To manage Your Account. Telegram ID (if telegram used) allows you to manage Your registration as a user of the Service. Telegram ID is neccessary to give You access to different functionalities of the Service that are available to You as a registered user.
To contact You. To contact You by email when it is neccessary. We do not verify your email, so if it is incorrect, we will can not to contact you at all
The Company will retain Your Personal Data only for as long as is necessary for the purposes set out in this Privacy Policy. We will retain and use Your Personal Data to the extent necessary to comply with our legal obligations (for example, if we are required to retain your data to comply with applicable laws), resolve disputes, and enforce our legal agreements and policies.
You have the right to request that We assist in deleting the Personal Data that We have collected about You.
You may update, amend, or delete Your information at any time by signing in to Your Account, if you have one, and visiting the account settings section that allows you to manage Your personal information. You may also contact Us to request access to, correct, or delete any personal information that You have provided to Us.
Please note, however, that We may need to retain certain information when we have a legal obligation or lawful basis to do so.
We can transfer or disclosure your personal data only if the Company is required to do so by law enforcement or in response to valid requests by public authorities (e.g. a court or a government agency).
The security of Your Personal Data is important to Us, but remember that no method of transmission over the Internet, or method of electronic storage is 100% secure. While We strive to use commercially acceptable means to protect Your Personal Data, We cannot guarantee its absolute security.
Our Service does not address anyone under the age of 18. We do not knowingly collect personally identifiable information from anyone under the age of 18. If You are a parent or guardian and You are aware that Your child has provided Us with Personal Data, please contact Us. If We become aware that We have collected Personal Data from anyone under the age of 18 without verification of parental consent, We take steps to remove that information from Our servers.
Our Service may contain links to other websites that are not operated by Us. If You click on a third party link, You will be directed to that third party's site. We strongly advise You to review the Privacy Policy of every site You visit.
We have no control over and assume no responsibility for the content, privacy policies or practices of any third party sites or services.
We may update Our Privacy Policy from time to time. We will notify You of any changes by posting the new Privacy Policy on this page.
You are advised to review this Privacy Policy periodically for any changes. Changes to this Privacy Policy are effective when they are posted on this page.
If you have any questions about this Privacy Policy, You can contact us: